Cybersecurity Alerts: 5 Critical Threats for Early 2025

Early 2025 brings new cybersecurity challenges, including sophisticated AI-driven attacks and enhanced ransomware, demanding immediate and proactive defense strategies from organizations and individuals alike.
The digital landscape is constantly evolving, and with it, the sophistication of cyber threats. As we approach early 2025, new and intensified dangers loom, requiring immediate attention and robust defenses. This article provides crucial cybersecurity alerts 2025, detailing five critical threats emerging in the coming year and offering actionable strategies to respond now, safeguarding your digital presence and assets.
The evolving threat landscape: what to expect in 2025
The year 2025 is poised to witness a significant escalation in cyber threats, driven by advancements in artificial intelligence, increasing reliance on cloud infrastructure, and the growing interconnectedness of our digital lives. Cybercriminals are becoming more organized, leveraging sophisticated tools and techniques that blur the lines between traditional hacking and advanced persistent threats. Understanding this evolving landscape is the first step toward effective defense.
Organizations and individuals must move beyond reactive security measures and adopt a proactive stance. The sheer volume and complexity of attacks mean that even well-protected entities can fall victim if their defenses are not continuously updated and rigorously tested. Anticipating future threats allows for the implementation of preventative controls, significantly reducing the attack surface and potential impact.
AI-powered attacks and defensive countermeasures
- Automated phishing: AI will generate highly personalized and convincing phishing emails, making them almost indistinguishable from legitimate communications.
- Deepfake social engineering: Voice and video deepfakes will be used to impersonate executives or trusted individuals, tricking employees into divulging sensitive information or authorizing fraudulent transactions.
- Adaptive malware: AI-driven malware will be capable of learning from its environment, evading detection, and adapting its attack vectors in real-time.
Responding to these AI-powered threats requires equally advanced AI-driven defenses. Machine learning models can analyze vast amounts of data to detect anomalies and predict attack patterns faster than human analysts. Implementing AI-powered endpoint detection and response (EDR) solutions, alongside advanced threat intelligence platforms, will be crucial. Employee training must also evolve to include recognition of deepfake and AI-generated content.
The battle against AI-powered threats will be a continuous arms race. Organizations must invest in security solutions that leverage AI and machine learning for both detection and prevention, ensuring their defenses are as intelligent and adaptive as the threats they face. Staying informed about the latest AI security research and best practices will be paramount for maintaining a strong security posture.
Critical threat 1: sophisticated ransomware 2.0
Ransomware has been a persistent nightmare for years, but in early 2025, we anticipate the emergence of ‘Ransomware 2.0’ – a far more insidious and damaging iteration. This new wave will combine advanced encryption with sophisticated data exfiltration techniques, making recovery more challenging and the financial and reputational impact even greater. Attackers will not only encrypt data but also steal it, threatening to publish or sell sensitive information if the ransom is not paid.
The primary vectors for these attacks will remain phishing and exploiting unpatched vulnerabilities, but with increased precision and automation. Cybercriminals will leverage AI to craft highly convincing lures and to identify vulnerable targets more efficiently. The targeting will be less indiscriminate, focusing on organizations with critical data and a higher likelihood of paying large ransoms.
Enhanced extortion tactics and double-extortion schemes
- Triple extortion: Beyond encryption and data publication, attackers will involve third parties, such as customers or business partners, to pressure victims into paying.
- Supply chain targeting: Ransomware groups will increasingly target weak links in supply chains, impacting multiple organizations simultaneously.
- Operational disruption: Attacks will focus on disrupting critical operational technology (OT) systems, causing widespread outages and potentially endangering lives in sectors like healthcare and critical infrastructure.
To combat Ransomware 2.0, organizations must strengthen their incident response plans, focusing on rapid detection, isolation, and recovery. Immutable backups, stored offline and off-site, are non-negotiable. Furthermore, advanced endpoint protection, network segmentation, and proactive vulnerability management will be essential. Employee awareness training should specifically address sophisticated phishing techniques and the dangers of clicking on suspicious links or attachments.
The response to sophisticated ransomware must be multi-layered, encompassing technological safeguards, robust policies, and continuous education. Investing in threat intelligence that specifically tracks ransomware group tactics, techniques, and procedures (TTPs) can provide a crucial advantage in anticipating and mitigating these devastating attacks.
Critical threat 2: supply chain vulnerabilities exploited
The interconnected nature of modern business means that a compromise in one vendor or partner can have catastrophic ripple effects across an entire ecosystem. In early 2025, we anticipate a significant increase in sophisticated supply chain attacks, where threat actors target less secure components or third-party software providers to gain access to their primary targets. This method allows attackers to bypass robust direct defenses.
These attacks often exploit trusted relationships, making them particularly difficult to detect. A malicious update to a widely used software library, a compromised hardware component, or a breach in a managed service provider (MSP) can inadvertently introduce vulnerabilities into hundreds or thousands of client networks. The impact can be widespread, affecting data integrity, operational continuity, and customer trust.
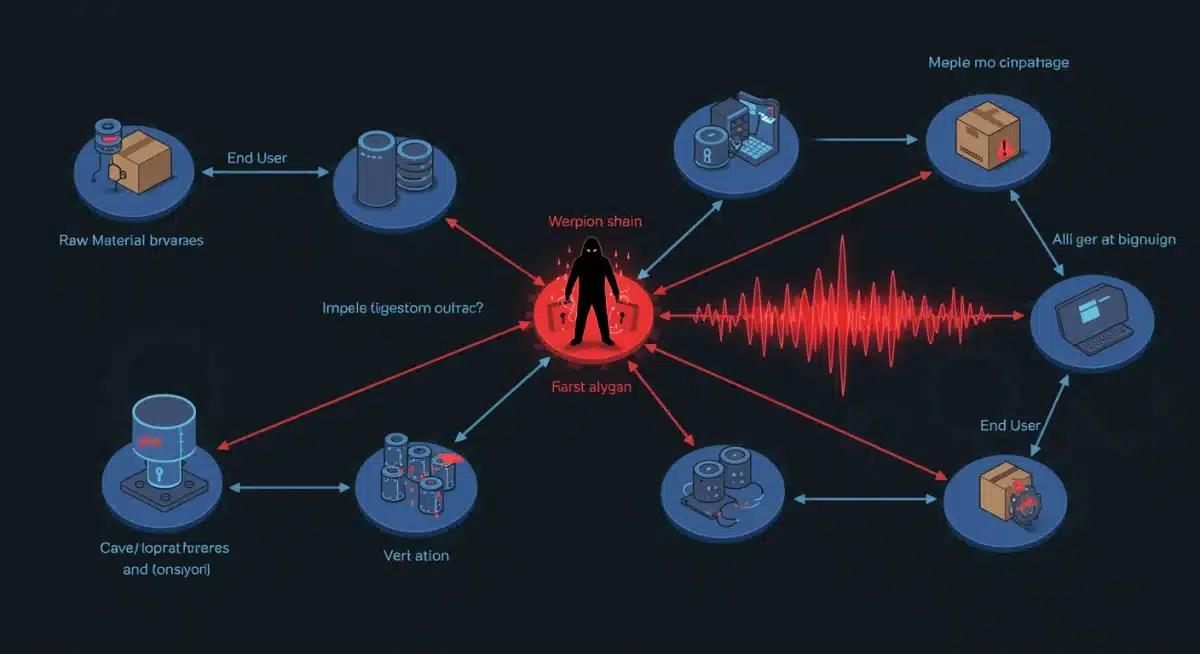

Securing the extended enterprise
- Vendor risk management: Implement rigorous vetting processes for all third-party vendors, assessing their cybersecurity posture and contractual obligations.
- Software bill of materials (SBOM): Demand and utilize SBOMs to understand the components within third-party software and identify potential vulnerabilities.
- Continuous monitoring: Monitor all third-party access and integrations for unusual activity or signs of compromise.
Organizations must extend their security perimeter beyond their immediate infrastructure to encompass their entire supply chain. This involves conducting regular security audits of vendors, enforcing strong contractual security clauses, and maintaining clear communication channels for incident response. Zero-trust principles should be applied to all third-party access, ensuring that every connection is verified and least privilege access is enforced.
Proactive measures, such as threat intelligence sharing within industry groups and continuous monitoring of software dependencies, can help identify and mitigate potential supply chain risks before they are exploited. Building resilience into the supply chain through redundancy and diversification of vendors can also limit the impact of a single point of failure.
Critical threat 3: advanced persistent threats (APTs) targeting critical infrastructure
State-sponsored and highly sophisticated criminal groups will increasingly focus their efforts on critical infrastructure in early 2025. These Advanced Persistent Threats (APTs) are characterized by their stealth, persistence, and deep understanding of their targets. They aim for long-term access to systems, not just immediate financial gain, often with geopolitical or industrial espionage motives. Sectors like energy, water, transportation, and healthcare are particularly vulnerable.
APTs often utilize zero-day exploits, custom malware, and living-off-the-land techniques to remain undetected for extended periods. Their objective is to gain control over operational technology (OT) systems, potentially disrupting essential services, causing physical damage, or stealing highly sensitive national secrets. The impact of such attacks can be devastating, affecting national security and public safety.
Defending against highly motivated adversaries
Protecting critical infrastructure requires a multi-faceted approach that integrates IT and OT security. This includes rigorous network segmentation, intrusion detection and prevention systems specifically designed for OT environments, and continuous vulnerability assessments. Regular security audits and penetration testing, simulating APT-level attacks, are also essential to identify weaknesses.
Collaboration between government agencies, industry partners, and cybersecurity experts is vital for sharing threat intelligence and developing collective defense strategies. Implementing robust identity and access management (IAM) solutions, especially multi-factor authentication (MFA) for all critical systems, remains a fundamental defense. Furthermore, developing comprehensive incident response plans that account for physical and operational impacts is crucial.
The unique challenges of securing critical infrastructure demand a specialized and integrated security strategy. Organizations in these sectors must prioritize investments in specialized security talent, advanced threat detection technologies, and participate actively in industry-specific threat information sharing initiatives to stay ahead of these persistent and dangerous adversaries.
Critical threat 4: identity theft and credential stuffing at scale
With the proliferation of online services and the increasing volume of data breaches, identity theft and credential stuffing attacks are set to reach unprecedented scales in early 2025. Cybercriminals continuously collect vast databases of stolen credentials, which they then use to automate login attempts across various platforms. The reuse of passwords across multiple accounts makes this tactic highly effective.
The consequences of successful credential stuffing attacks range from unauthorized access to financial accounts and personal data to corporate espionage and system compromise. For individuals, it can lead to severe financial loss and reputational damage. For organizations, it can result in data breaches, regulatory fines, and a significant erosion of customer trust. The sheer volume of these attacks makes manual detection nearly impossible.
Protecting digital identities
- Multi-factor authentication (MFA): Implement MFA for all accounts, making it significantly harder for attackers to gain access even with stolen credentials.
- Unique and strong passwords: Encourage or enforce the use of unique, complex passwords for every service, ideally using a password manager.
- Behavioral analytics: Utilize systems that monitor user behavior for anomalies, such as unusual login locations or access patterns, to detect potential compromises.
Organizations must implement robust identity and access management (IAM) solutions that include strong authentication mechanisms and continuous monitoring. For individuals, adopting a password manager and enabling MFA on all available services are the most effective personal defenses. Regularly checking for personal data breaches through services like ‘Have I Been Pwned’ can also provide early warnings.
The fight against identity theft and credential stuffing requires both technological solutions and user education. By making it harder for attackers to leverage stolen credentials, we can significantly reduce the success rate of these widespread attacks and protect both individual and organizational digital identities.
Critical threat 5: zero-day exploits and rapid patch cycles
Zero-day exploits, which leverage vulnerabilities unknown to software vendors, will continue to be a significant threat in early 2025. However, what will intensify is the speed at which these exploits are discovered, weaponized, and then patched. The window of opportunity for attackers to exploit a zero-day vulnerability before a patch is released is shrinking, but the damage inflicted during that short period can be substantial.
This rapid cycle demands extreme agility from both defenders and attackers. Organizations must be prepared for swift action, implementing emergency patching procedures and having robust incident response capabilities to contain and mitigate the impact of zero-day attacks. The challenge lies in identifying and responding to these unknown threats before they cause widespread damage.
Accelerating defense and response
- Vulnerability management: Implement continuous vulnerability scanning and penetration testing to proactively identify and address potential weaknesses.
- Threat intelligence: Subscribe to advanced threat intelligence feeds that provide early warnings about emerging zero-day threats and exploit kits.
- Endpoint protection: Deploy advanced endpoint detection and response (EDR) solutions that can detect anomalous behavior indicative of zero-day exploitation, even without known signatures.
To effectively counter zero-day exploits, organizations need to prioritize proactive security measures. This includes investing in security research, participating in bug bounty programs, and fostering a culture of rapid patching and continuous security improvement. Automated patching and configuration management tools can help accelerate the deployment of critical security updates across the infrastructure.
Furthermore, adopting a ‘assume breach’ mindset and focusing on detection and response capabilities can help limit the impact of zero-day attacks when they inevitably occur. By reducing the time between detection and remediation, organizations can minimize their exposure and recover more quickly from even the most sophisticated attacks.
How to build a resilient cybersecurity posture for 2025
Building a resilient cybersecurity posture for 2025 goes beyond simply reacting to threats; it requires a strategic, proactive, and adaptive approach. The convergence of advanced technologies, such as AI, with traditional attack vectors means that defenses must be multi-layered and continuously evolving. A strong security posture is not a one-time project but an ongoing commitment to protecting digital assets.
This involves a combination of robust technological solutions, well-defined policies and procedures, and a highly aware and trained workforce. The human element remains both the strongest and weakest link in the security chain, emphasizing the importance of continuous education and a culture of security awareness throughout the organization. Prioritizing cybersecurity at the executive level ensures adequate resources and strategic alignment.
Key pillars of a proactive defense strategy
- Zero-trust architecture: Implement a zero-trust model where no user or device is inherently trusted, requiring verification for every access request.
- Security awareness training: Conduct regular and engaging training for all employees, covering the latest threats like phishing, deepfakes, and social engineering.
- Incident response planning: Develop, test, and regularly update comprehensive incident response plans that detail roles, responsibilities, and procedures for various cyber incidents.
- Regular audits and assessments: Perform frequent security audits, penetration tests, and vulnerability assessments to identify and remediate weaknesses proactively.
Investing in advanced threat intelligence and security analytics platforms will provide the visibility needed to detect and respond to emerging threats quickly. Automating security tasks, such as vulnerability patching and log analysis, can free up security teams to focus on more strategic initiatives. Furthermore, fostering collaboration and information sharing with industry peers and government agencies can provide invaluable insights into the evolving threat landscape.
Ultimately, a resilient cybersecurity posture is built on a foundation of continuous improvement and adaptation. By embracing new technologies, empowering security teams, and instilling a security-first culture, organizations can navigate the complex threat landscape of 2025 with confidence and protect their most valuable assets from an ever-growing array of cyber dangers.
| Key Threat | Response Strategy |
|---|---|
| Sophisticated Ransomware | Implement immutable backups, advanced EDR, and enhanced incident response. |
| Supply Chain Exploits | Rigorously vet vendors, demand SBOMs, and apply zero-trust to third-party access. |
| APT Critical Infrastructure | Integrate IT/OT security, network segmentation, and collaborate on threat intelligence. |
| Zero-Day Exploits | Accelerate patch cycles, use advanced EDR, and leverage threat intelligence. |
Frequently asked questions about 2025 cybersecurity threats
While many threats are evolving, the most significant risk in early 2025 is expected to be sophisticated ransomware 2.0. This new variant combines advanced encryption with data exfiltration, making recovery harder and increasing the potential for triple extortion tactics, impacting both data and reputation.
To combat AI-powered attacks, organizations should invest in AI-driven defensive tools like advanced EDR. Furthermore, employee training must be updated to recognize AI-generated phishing and deepfakes. Continuous threat intelligence and security research are also crucial for staying ahead.
Effective measures include rigorous vendor risk management, demanding Software Bill of Materials (SBOMs) from suppliers, and continuous monitoring of third-party access. Implementing zero-trust principles for all external integrations is also vital to secure the extended enterprise.
MFA is crucial because it significantly enhances security against identity theft and credential stuffing. Even if attackers obtain passwords, MFA acts as an additional barrier, requiring a second verification factor, thereby preventing unauthorized access to accounts and sensitive data.
Critical infrastructure protection against APTs involves integrating IT and OT security, robust network segmentation, and specialized intrusion detection systems. Collaboration with government entities for threat intelligence sharing and conducting advanced penetration tests are also essential.
Conclusion
The cybersecurity landscape in early 2025 presents a formidable challenge, with threats evolving in sophistication and impact. From advanced ransomware and AI-powered attacks to exploited supply chains and persistent threats against critical infrastructure, the need for proactive and resilient defense strategies has never been more urgent. Organizations and individuals must prioritize continuous education, robust technological investments, and a culture of security awareness to safeguard their digital assets. By understanding these critical cybersecurity alerts 2025 and implementing the recommended responses now, we can collectively build a more secure future against the relentless tide of cybercrime.